Security Features
Security in Analytics has the following primary components:
-
Folders: All resources are located in folders. A folder can be secured so that only certain users have permission to view or interact with the resources within.
-
Roles: Roles define the specific permissions (tasks or actions) that can be performed by a particular type of user, such as viewing resources or managing resources.
-
Groups: Roles can be granted to a group which provide permissions to view or interact with the resources within certain folders. Those permissions are inherited by all users who are members of the group.
-
Users: Each person who should have any access to Analytics should have a user account created. Roles can then be granted to the user (either directly or via group membership) which provide permissions to view or interact with the resources within certain folders. The same user may have different roles (and therefore a different level of access) to different folders.
About Folder-based Security
The Analytics folder tree defines the hierarchical structure of resources in the system. It is typically used to recreate the organizational structure so that resources that are owned by a particular part of the business can be located in the appropriate folder. Then, access to view or manage those resources can be controlled by security permissions. See also Folders.
Security management in Analytics is folder based, so the folder hierarchy needs to be structured with the business' security needs in mind. If there is a specific area of the business that should be visible to or manageable by some users and not others, then that business area needs to have its own folder. The folder can optionally include sub-folders for organizing the resources within.
Users are granted permissions to perform certain tasks within a given folder. These permissions can extend to any sub-folders below.
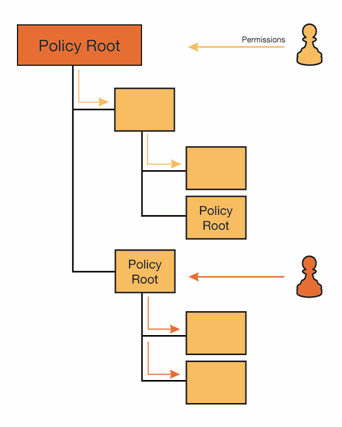
Inheritance and Policy Root Folders
A folders can either be a policy root or have an inherited policy:
-
Policy Root: A folder in which a security policy is defined. The security policy consists of permissions – a list of users and groups are granted permissions to perform particular actions on resources within the folder (and by extension, its inherited sub-folders).
-
Inherited Policy: Security does not have to be set on every folder individually. Most folders inherit the permissions from the policy root folder above them in the folder hierarchy. This may be the parent folder, grand-parent folder, etc. Anything that a user can see or do in the policy root, they can also see or do in any inherited folders.
By default, the organization root folder is a policy root and all folders below it inherit their permissions. This means that you set permissions once and those same permissions are applied across your organization.
If you require a more fine-grained approach to security then you can select folders in the hierarchy which should have separate permissions and “break the inheritance” by configuring them as policy roots in their own right. For example, if your hierarchy includes multiple departments then you may wish to configure each department folder to be a policy root so that a given user can be granted access to one department but not another.
Folders and Security Policies
Related Information